Run Validator Node
The Opera client was previously referred to as the "Opera client powered by Sonic technology", or simply, the "Sonic client".
However, given that the name "Sonic" has now been reserved for our new, upcoming network, any mention of "Sonic" on these pages, GitHub, or pieces of code, refers to the current Opera client.
Validator Parameters
Minimum Stake: 50,000 FTM.
Maximum Validator Size: 15x the self-stake amount.
Rewards: Currently ~6% APR (normal APR for self-stake + 15% of delegators' rewards). APR varies based on the amount of FTM staked on the entire network. For up-to-date APR, check our website.
Steps to Run Validator
1. Launch a Server Instance
You can run your validator node on dedicated hardware (also called bare metal) or use a cloud provider. We recommend choosing one of the established cloud providers, e.g. Google GCP or Amazon AWS.
Node Hardware Specifications
To run the node software, you need at least 4 vCPUs and 32 GB of RAM. We recommend getting at least 1 Gbps of redundant backbone connectivity to allow a stable and uninterrupted network traffic flow.
You will also need at least 1 TB of local SSD/NVMe storage. Remotely connected storage systems, e.g., Amazon EBS, usually don't provide the latency and random access performance the node requires. The Google GCP N2D instances with local SSD drives or Amazon AWS i3en.xlarge with the instance storage match the minimal requirements.
We recommend going with Ubuntu LTS Server (64-bit) or a similar Linux distribution.
Required Storage Capacity
1 TB of local SSD/NVMe storage is sufficient for a pruned DB either on a validator or on a no-history pruned dataset.
6 TB of local SSD/NVMe is needed if you'd like to run a full-size (non-pruned) datadir.
Obtain the latest genesis file.
Network Settings
An Opera node requires both TCP and UDP network traffic to be allowed on port 5050 by default. A custom port can be used with --port <port> flag when running your node.
2. Install Required Development Tools
You need the essential building tools and Go compiler version 1.21 or newer to build the Opera client and bundled tools.
First, install the required build tools:
Install the latest Go compiler from binary distribution:
Set up Go language export paths:
3. Build the Opera Node Software
Building the Opera binary requires the essential software development tools and the Go language version 1.21 or newer to be available. The previous section contains basic steps to deploy the required applications on the recommended Linux distribution. Please refer to your operating system manuals to install the development tools needed for this step.
Please check the latest release of the Opera node and adjust your commands accordingly.
You can confirm the Opera release by executing the version subcommand on the created binary.
Optionally, you may want to copy the Opera node app and the tooling into the system-wide bin folder to make it available without explicitly specifying the binary path.
4. Prime the Opera Database
You need a valid state database to be able to participate in the network. The fastest and easiest way is to use a genesis file. Please check the official repository, where new signed genesis files are published, and pick the latest one suitable for a validator node. You will need approximately 50 GB of storage space for the genesis file download.
Download the latest genesis file and the corresponding checksum:
Check your download using the MD5 checksum file:
Use the Opera tooling to prime the state database using the downloaded genesis file. Refer to these steps to determine the amount of cache and memory consumption soft limit for your node.
The --datadir flag should point to your local NVMe storage mount path. The --mode validator flag tells the tool to create a minimal required state database for your node.
The Opera tool creates a primed state database from the genesis file. The last step is a validation procedure. It confirms that the expected state was built successfully reaching the expected root hash. You can refer to the official repository to verify that the state hash is indeed correct.
Calculate Cache Size and Memory Consumption Soft Limit Values
The Opera node utilizes a large amount of RAM to achieve great speed and responsiveness. It should be the only user-space application consuming your system resources.
Approximately 40% of the available RAM should be used as the
--cachefor both thesonictoolandsonicdapplications. The final value is denominated in MiB. For example: 64,000 MiB RAM * 40% = 25,600 MiB. You should never set the value below 10,000 MiB.Approximately 90% of the available RAM should be used as the application memory consumption limit. This limit is controlled by the
GOMEMLIMITenvironment variable. The final value includes abbreviated units. We recommend usingGiBfor simplicity. For example: 64 GiB RAM * 90% ≈ 58 GiB.
5. Synchronize With the Network
Your node database has been primed to a certain epoch in the past using a genesis file and the Opera tool. Now you need to get the node up to the current state.
To do it, your node needs to be started in the read-only mode and establish a connection with the network. Please make sure your firewall is configured correctly to allow such communication. The amount of memory dedicated to the node cache and the memory consumption limit are outlined above.
The Opera node should start and connect with the network, advancing the state by creating and processing new blocks. Please notice the age part of the log message, which tells you how far in the past these blocks are. The age should not exceed a couple of seconds once the node is fully synchronized.
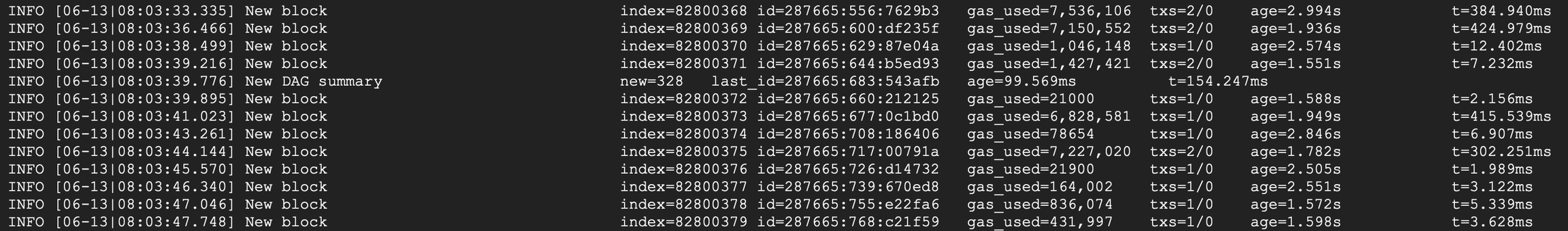
6. Create a Validator Wallet
Your Opera node is up and running in the read-only mode, synchronizing with the network. Now you need to create a wallet that will identify and control your validator account.
The Opera tool does contain a utility function to create such a wallet, but we strongly recommend doing it off the server and in a secure way. The best approach is to use one of the hardware wallets available on the market or a trustworthy software wallet capable of sending transactions to the Opera network.
Make sure to keep the validator wallet private and secure. Never share this wallet or the corresponding key with anyone. The safety of your validator funds depends on it.
Once your validator wallet is created, you need to put the initial amount of funds in it. The registration process involves placing these funds as a stake in your account. If you don't have native FTM available on your Opera wallet already, you may need to purchase them using a crypto exchange.
7. Create a Validator Signing Key
An Opera validator node signs special types of messages broadcasted to the Opera network. A sequence of these messages from the confirmed active validators is what allows the network to process transactions safely and securely. Your node needs a signing key to be able to participate. Use the Opera tool to create this key on the server.
Please back up your consensus signing key safely. You may need to deploy it on a new server in case of a hardware or software failure.
The key cannot be used to access your funds, but it can be utilized to invoke a double-sign error, which is penalized. Please handle your validator key with proper care.
Create the validator signing key on the node server:
Follow the prompts and supply a secure password:
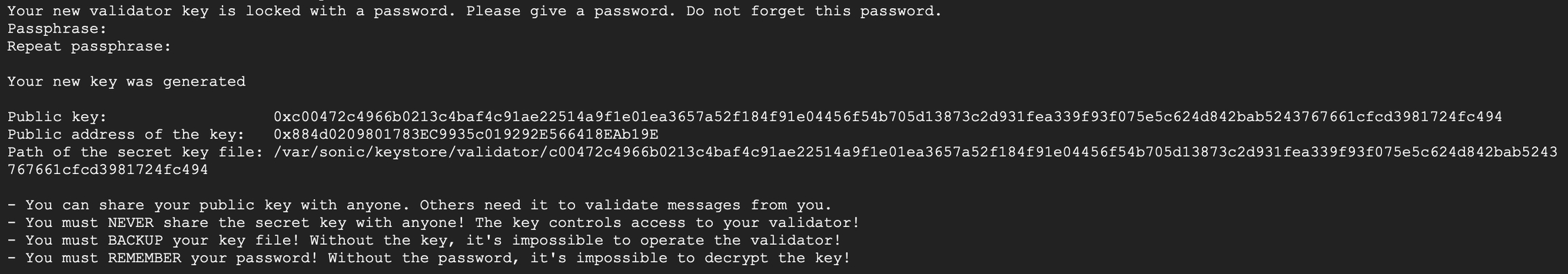
Notice the public key part of the application output message starting with 0xc00472c4966b0213…. This is the public key used in the registration process in the next step to let the network know what key is going to be used by your node as its distinct signature.
Note that the picture above demonstrates the output of the validator key creation. Your real public key and the path to the key file will be different.
8. Register Your Validator
The network needs to be aware of your validator key to accept it. The registration process is done by invoking a smart contract called SFC. This contract is responsible for the management of stakes and related rewards.
You can find the SFC contract here: 0xFC00FACE00000000000000000000000000000000
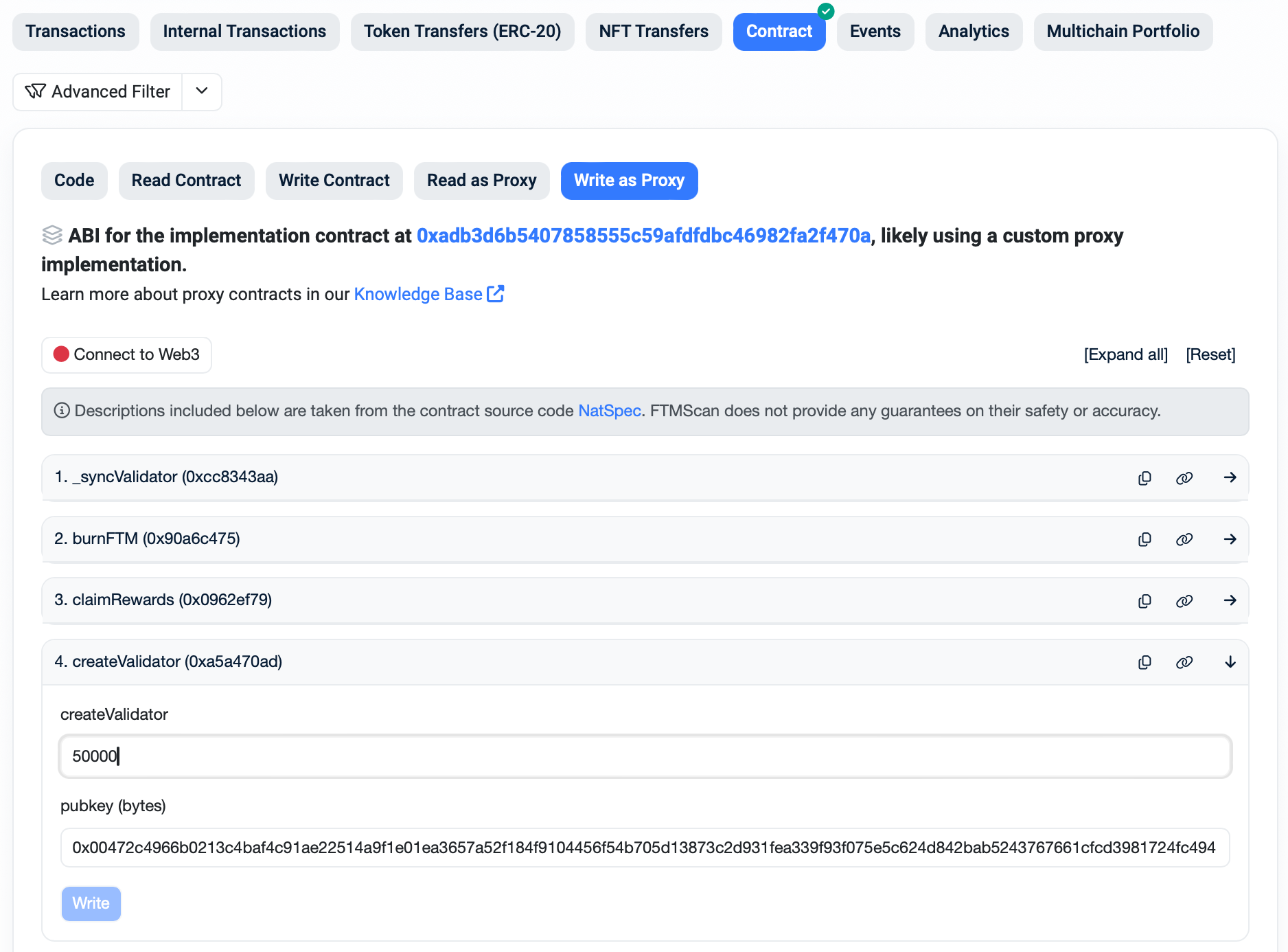
You can use the Explorer to invoke the appropriate registration function called createValidator. You will need to include at least the minimal stake to be able to finish the registration. The "pubkey" field is going to contain the public key created in the previous step. Use the validator wallet key to sign the registration transaction.
If you want to interact with the SFC contract directly, please use the latest available ABI for the interface definition.
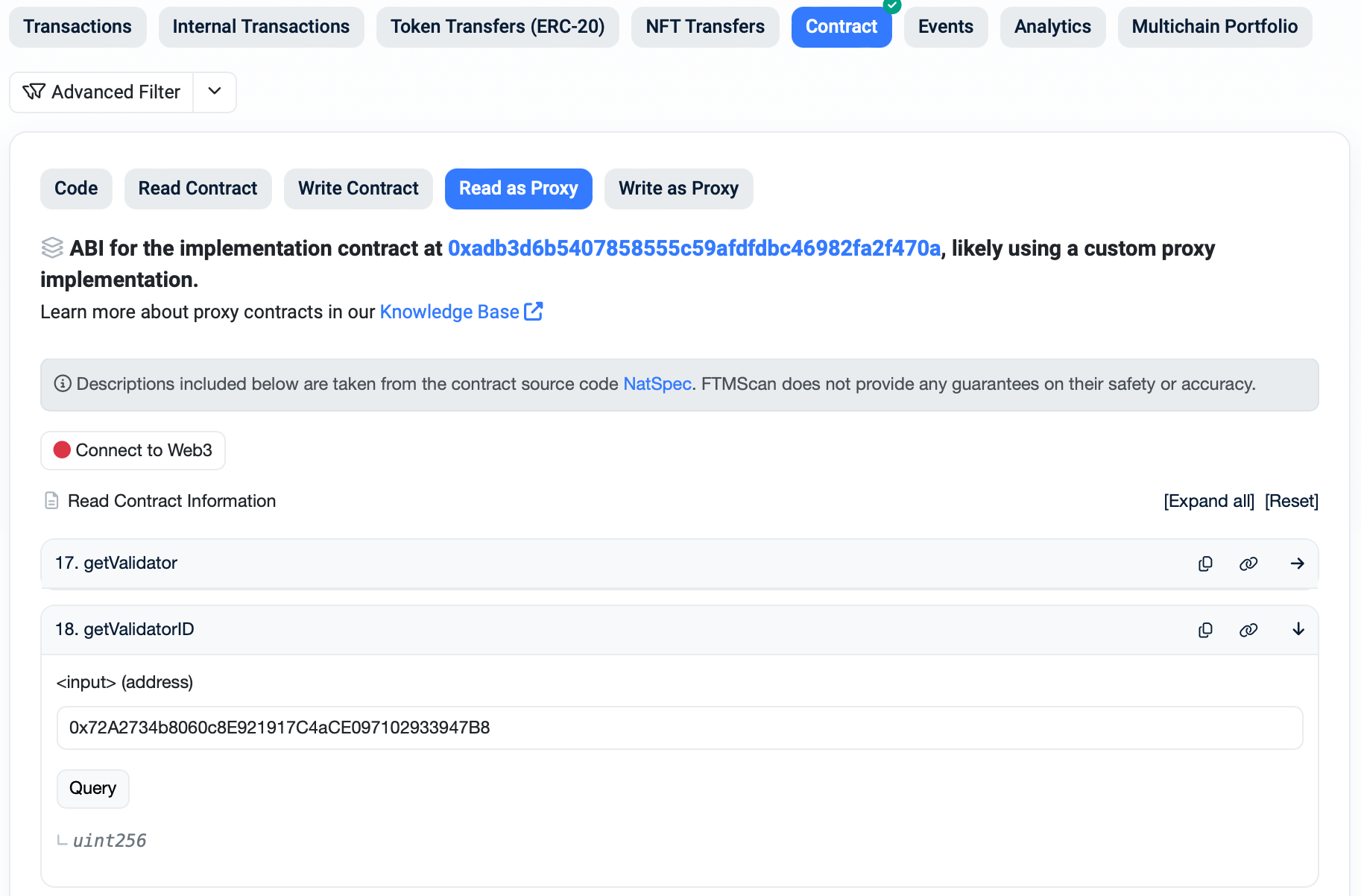
Once your registration is confirmed, you can use the Explorer to get the ID assigned to your validator. The SFC allows you to query this ID for your specific validator wallet using getValidatorID function.
9. Run Your Validator Node
You are almost done. Now you need to restart your running node with the validator signing key unlocked. Please make sure your node is already synchronized with the network before proceeding.
Stop the Opera application and wait until the node gracefully terminates:
The Opera node may run for several minutes until it stops. Please make sure to never terminate it forcefully. If the Opera node cannot properly close its persistent database, you will have to restore the database from a backup or a genesis file again.
Start the Opera node again, adding your validator public key and the validator ID. If you start your node in a non-interactive environment, e.g. as a dystemd service, you may need to add a path to the password file so the validator key can be unlocked. Alternatively, you can use a detached terminal (i.e. tmux) to run the node. In that case, the node will ask for the password when started.
Next Steps
Congratulations! Your validator node is up and running. Now you may be wondering what to do next. You can find some useful hints below.
Validator Name and Logo on the Explorer
If you'd like to set up a name and logo for your node, please check the this repository for additional information and guides.
Community and Help
The important part of running a validator on Opera is the community.
We would like our validators to get involved in the network's future. fWallet allows you to use your stake to vote for important changes in the network configuration and development. You can also check our social channels for additional information about upcoming events, upgrades, and planned governance votes. If you have any problems with the node, our awesome participants are ready to provide additional information and help.
Monitoring and Health
Each validator is expected to actively maintain their node and participate in securing the network traffic, but we realize accidents happen. If your node drops offline, the Explorer will show its address as being in maintenance mode. You can also check a simplified HTTP interface with a list of nodes that did not emit new consensus events recently.
If your node is not running properly for a short time, nothing happens. You will not receive any rewards during the downtime, but this is the only consequence. If your node is offline for more than 5 days, or if it's constantly dropping off the network, the guarding algorithm will suspend your validator wallet and the signing key in the SFC contract. In that case, you will not be able to join again and the only option would be to withdraw your stake and start over.
Last updated